Duo Trusted Endpoints - Google Workspace (formerly known as G Suite) Managed Device Deployment
Last updated:
Overview
Duo's Trusted Endpoints feature secures your sensitive applications by ensuring that only known devices can access Duo protected services. When a user authenticates via the Duo Prompt, we'll check for the access device's management status. You can monitor access to your applications from trusted and untrusted devices, and optionally block access from devices not trusted by your organization.
Trusted Endpoints is part of the Duo Essentials, Duo Advantage, and Duo Premier plans.
Before enabling the Trusted Endpoints policy on your applications, you'll need to configure your managed mobile devices. This guide walks you through Google Workspace configuration for Android and iOS mobile devices.
Note that this Duo Google Workspace management integration and the Duo Mobile management integration for verifying endpoints are mutually exclusive. You won't be able to use Google Workspace for verification if a management integration for Duo Mobile exists.
Mobile Trusted Endpoints and Verified Duo Push: Trusted endpoint verification of iOS and Android devices with Duo Mobile uses the standard Duo Push approval process and will not prompt for a Duo Push verification code, even if the effective authentication methods policy for the user and application has "Verified Duo Push" enabled.
Prerequisites
- Access to the Duo Admin Panel as an administrator with the Owner, Administrator, or Application Manager administrative roles.
- A Google Workspace Business or Enterprise plan.
- Access to the Google Workspace console as an administrator with the rights to manage apps on iOS and Android devices and enroll devices.
Enable Advanced Mobile Management
-
Log on to the Workspace Admin console as an administrator and click on Devices.
-
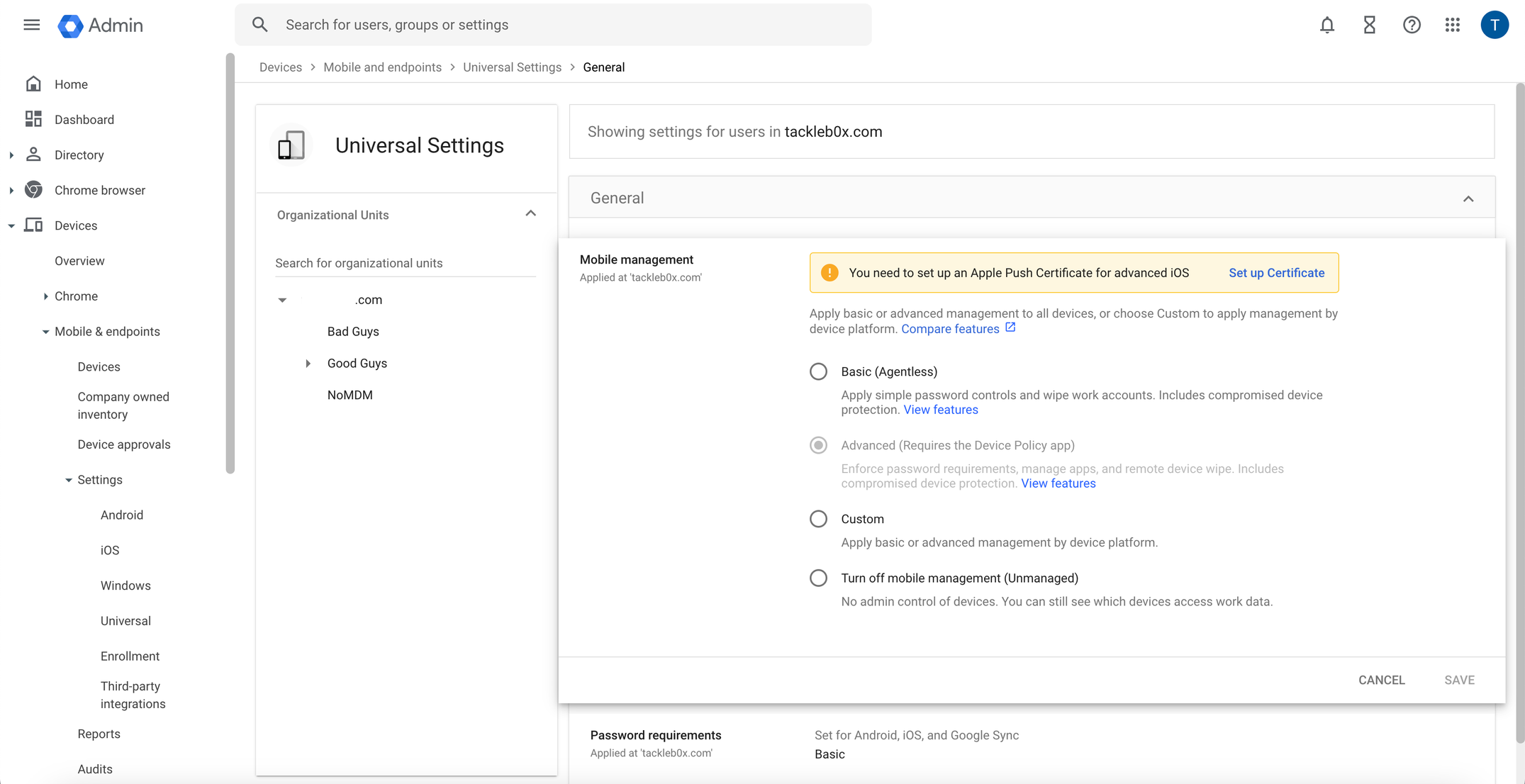
Click on the Mobile & endpoints drop-down menu, select Settings → Universal, and click on the "General" section.
-
Choose Mobile Management and then select the Advanced option.
-
Click Save to apply the new mobile settings.
Android Configuration
Duo determines trusted device status on Android devices by leveraging the installed and activated managed Duo Mobile application on a given device to verify device information.
Use the following instructions to complete setup of your Duo Google Workspace management integration for Android devices.
Create the Google Workspace Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Trusted Endpoint Integrations" page, locate Google Workspace in the list of integrations.
- Choose Android from the "Select operating system" drop-down, and then click the Add button.
The new Google Workspace integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration takes advantage of managed app configuration and therefore Duo Mobile must be installed by your MDM for the device to be considered trusted.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Google Workspace management integration page to complete the configuration steps.
Add Duo Mobile as a Managed Application
-
Click the Apps link on the left side of the console.
-
Select Web and mobile apps and click the Add app button on the top of the Workspace admin console to add a new managed application.
-
Select the Search for apps option from the drop-down.
-
Search for Duo Mobile. Click on the search result for Duo Mobile and then click Select.
-
Specify "User Access" and select "All users in your organization" or "Select groups and organizational units". Click Continue.
-
Select the Make this a managed app option. Click Finish.
-
You may change the approval and notification options if you wish. Click on the added app and when your changes are done, click Save.
Create a Managed Configuration for Duo Mobile
-
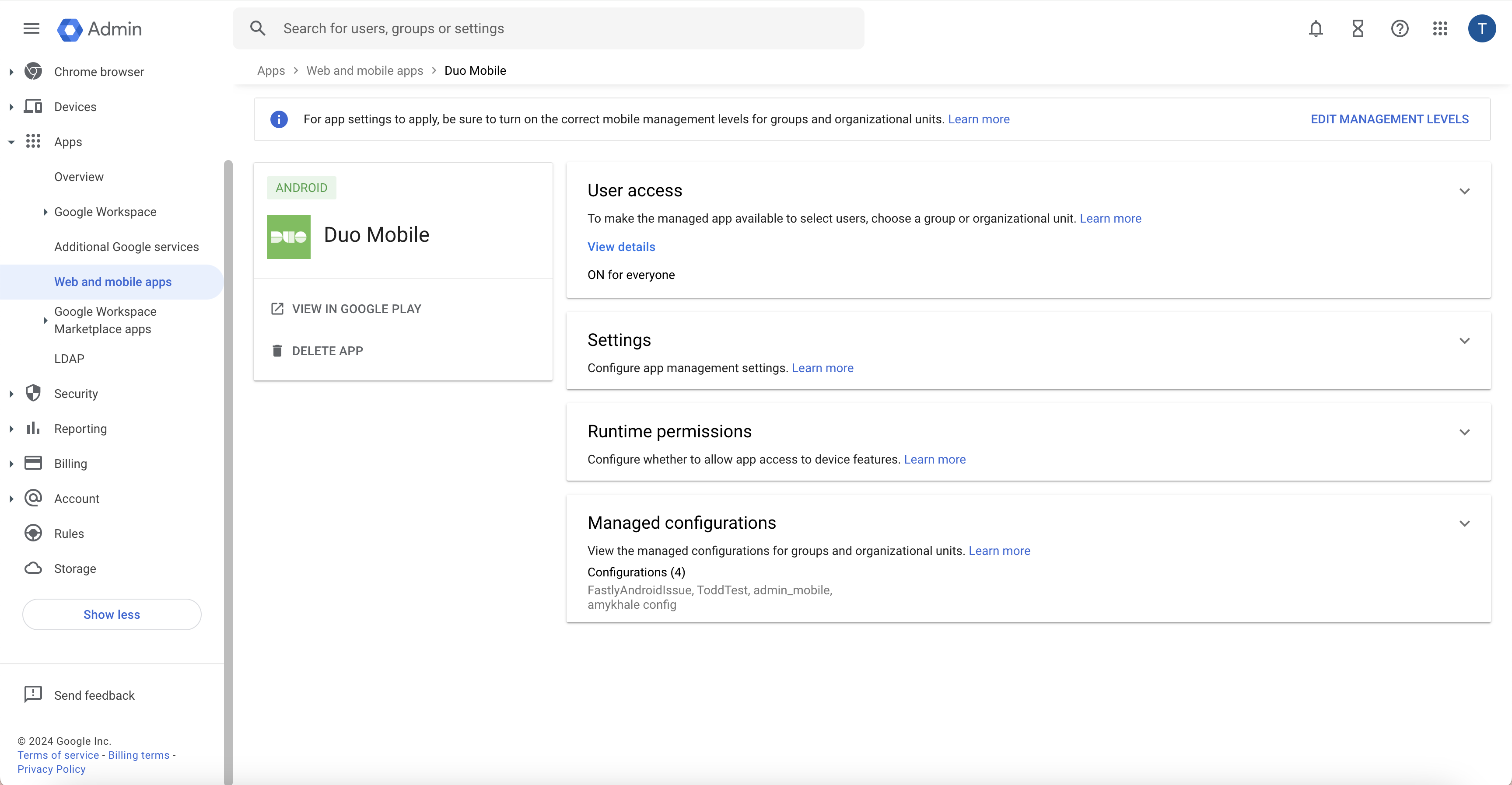
Click on Duo Mobile in the list of managed applications.
-
Click Managed Configurations at the bottom of the Duo Mobile page, and then click Add Managed Configuration. Give the configuration a name.
-
Return to your Google Workspace management integration page in the Duo Admin Panel.
-
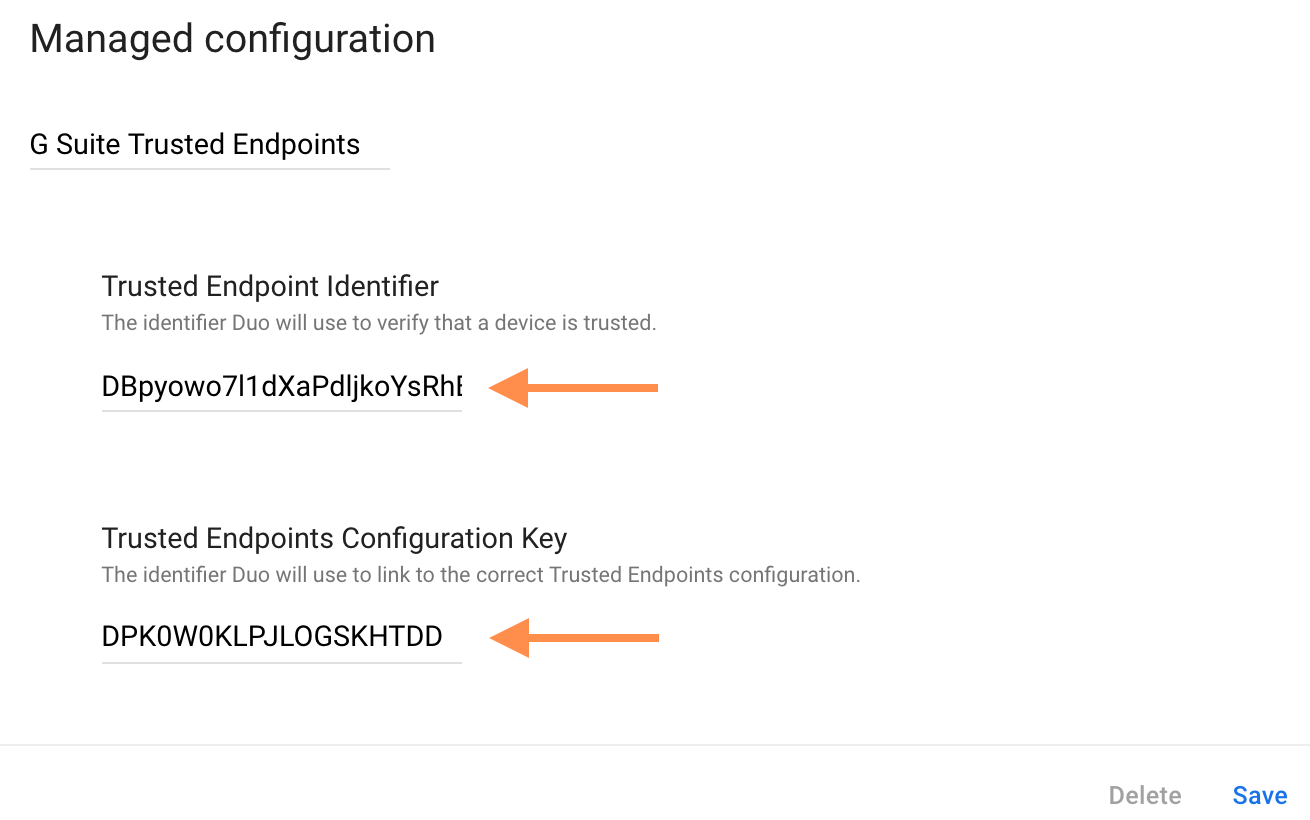
Copy the "Secret Key" value from the "Create a Managed Configuration" section of your Google Workspace management integration (it will look similar to DBpyowo7l1dXaPdljkoYsRhBtorOoylaltj1ovsH). Paste this in Workspace as the Trusted Endpoint Identifier value.
-
Copy the "Trusted Endpoints Configuration Key" value from the "Create a Managed Configuration" section of your Google Workspace management integration (it will look similar to DPK0W0KLPJLOGSKHTDD). Paste this in Workspace as the Trusted Endpoints Configuration Key value. Click Save after filling in both fields.
-
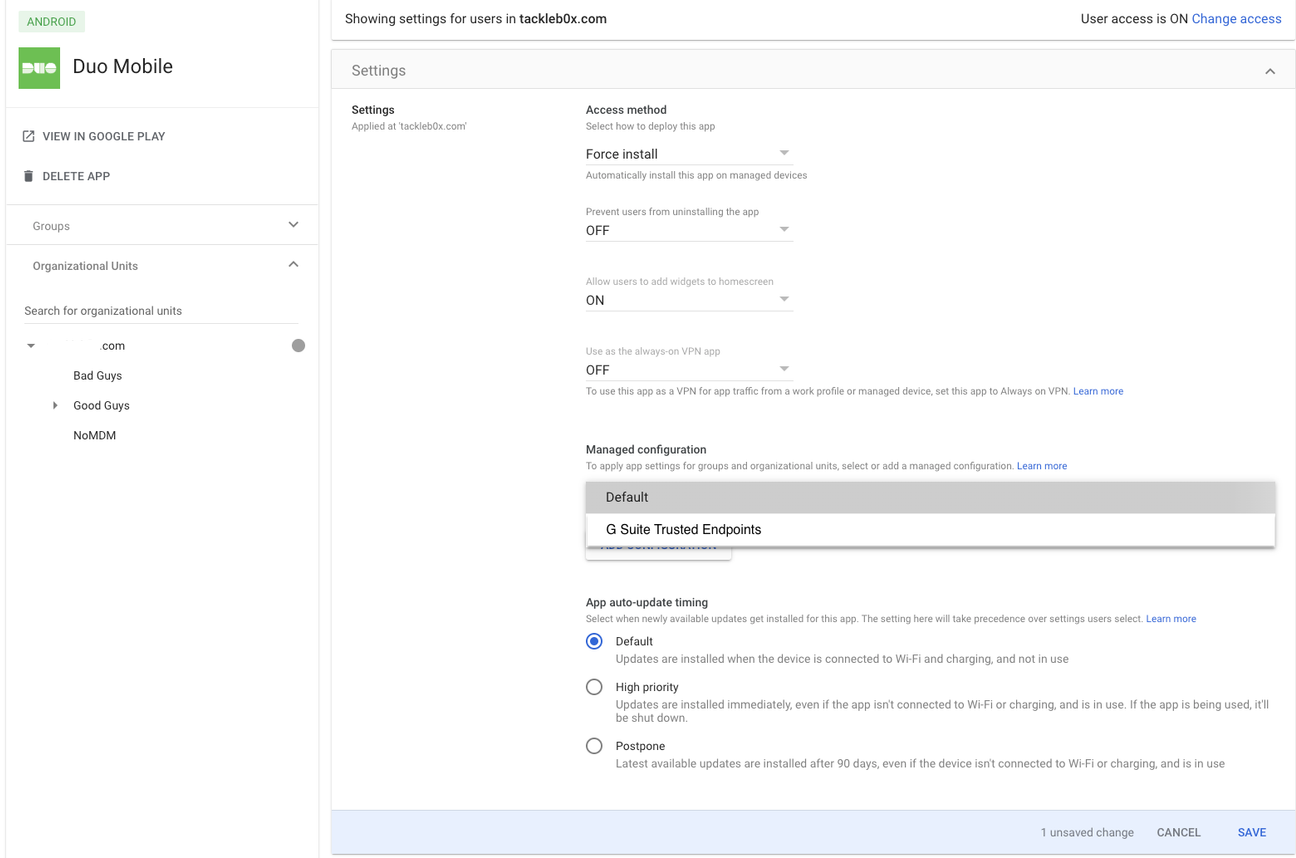
Go back to the Duo Mobile page and click Settings.
-
In the "Managed Configuration" section, select the managed configuration you just created and then click Save.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
iOS Configuration
Duo determines trusted device status on iOS devices by leveraging the installed and activated managed Duo Mobile application on a given device to verify device information.
Use the following instructions to complete setup of your Duo Google Workspace management integration for iOS devices.
Create the Google Workspace Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Trusted Endpoint Integrations" page, locate Google Workspace in the list of integrations.
- Choose iOS from the "Select operating system" drop-down, and then click the Add button.
The new Google Workspace integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration takes advantage of managed app configuration and therefore Duo Mobile must be installed by your MDM for the device to be considered trusted.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Google Workspace management integration page to complete the configuration steps.
Add Duo Mobile as a Managed Application
-
Click the Apps link on the left side of the console.
-
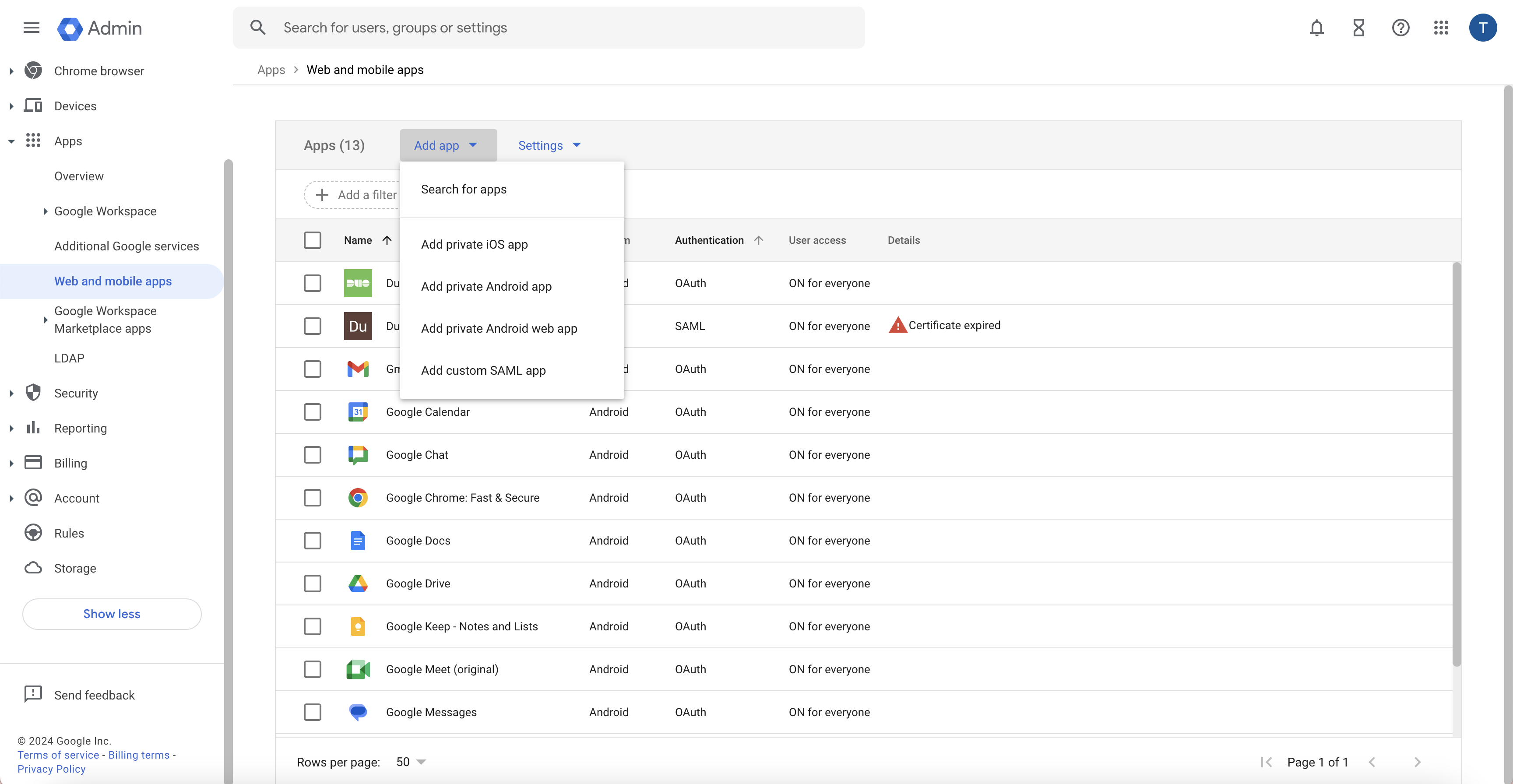
Select Web and mobile apps and click the Add app button on the top of the Workspace admin console to add a new managed application.
-
Click on Add app and select Add private iOS app in the drop-down.
-
Search for Duo Mobile. Click on the search result for Duo Mobile and then click Select.
-
Specify "User Access" and select "All users in your organization" or "Select groups and organizational units". Click Continue.
-
Specify "Access method" and select "Available" to allow users to download this app from the App Store or "Force install" to automatically install this app on managed devices. Click Finish.
-
You may change the approval and notification options if you wish. Click on the added app and when your changes are done, click Save.
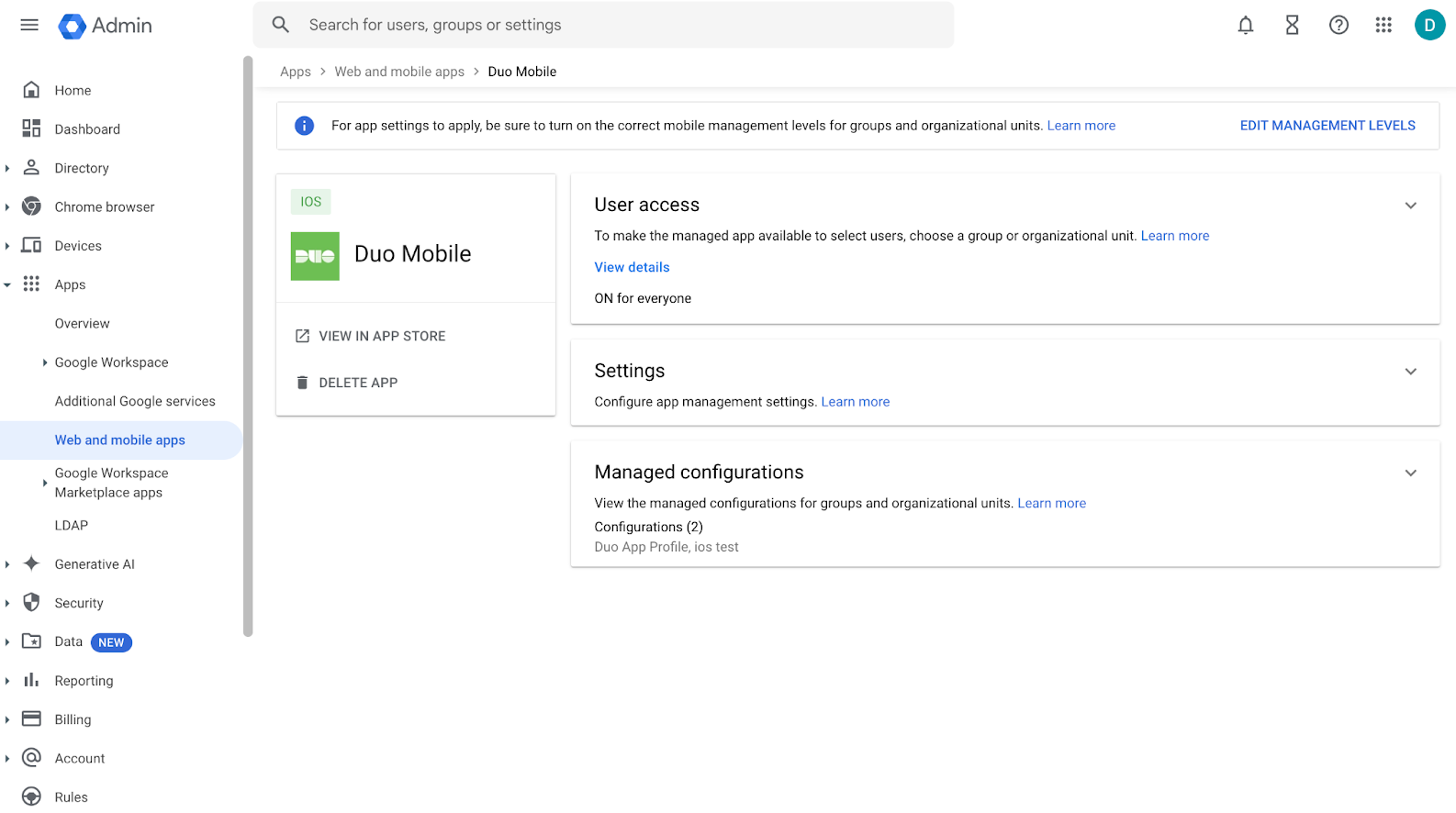
Create a Managed Configuration for Duo Mobile
-
Click on Duo Mobile in the list of managed applications.
-
Click Managed Configurations at the bottom of the Duo Mobile page, and then click Add Managed Configuration. Give the configuration a name.
-
Return to the Duo Admin Panel. Under "Create a Managed Configuration", copy the Application Configuration Key and paste it into the Workspace Trusted Endpoints XML Configuration Key field.
-
Click Save.
-
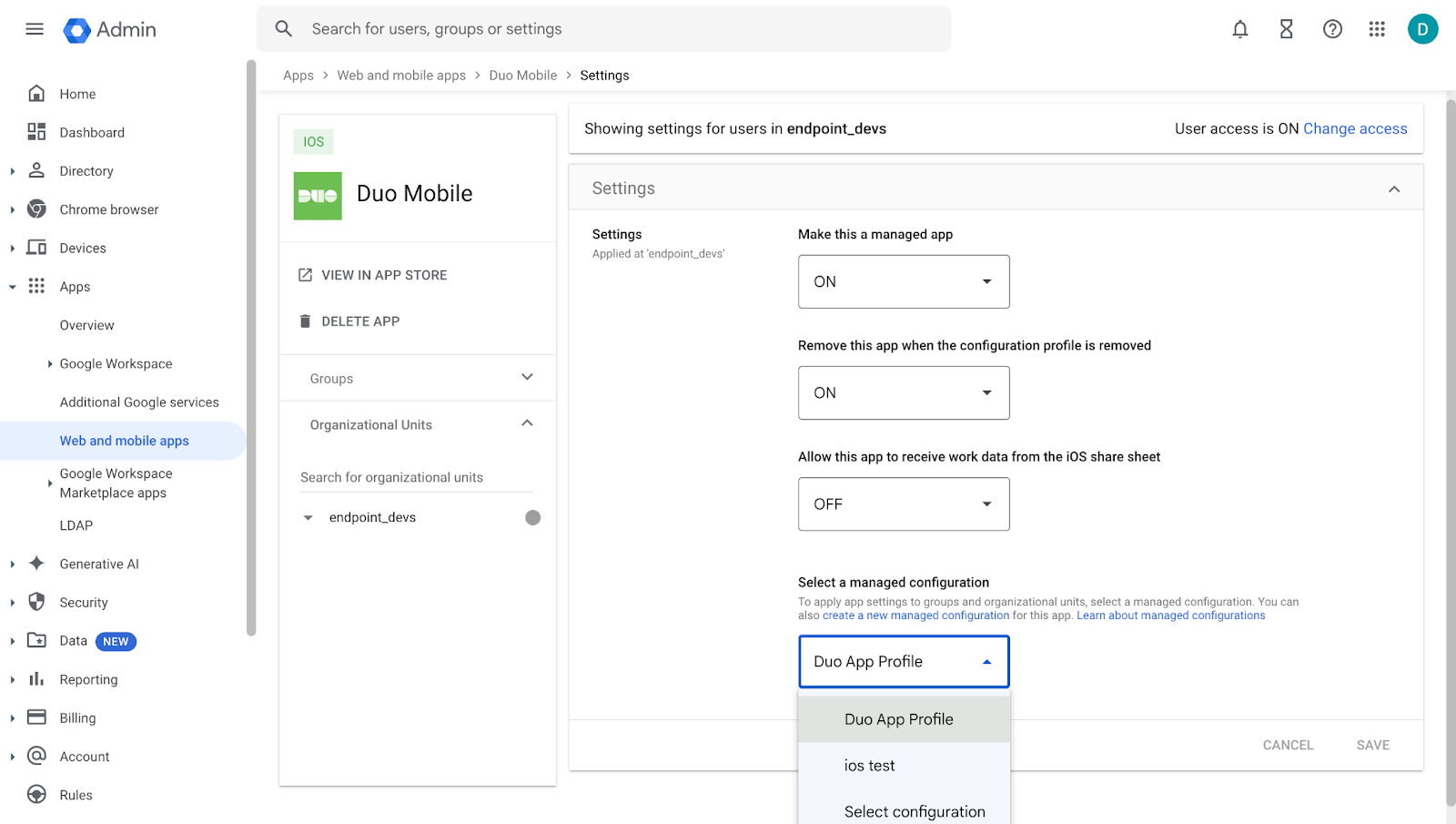
Go back to the Duo Mobile page and click Settings.
-
In the "Managed Configuration" section, select the managed configuration you just created and then click Save.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Finish Trusted Endpoints Deployment
Once your Workspace managed devices receive the Duo config you can set the Trusted Endpoints policy to start checking for managed device status as users authenticate to Duo-protected services and applications.
When your trusted endpoints policy is applied to your Duo applications, return to the Google Workspace trusted endpoint management integration in the Admin Panel. The "Change Integration Status" section of the page shows the current integration status (disabled by default after creation). You can choose to either activate this management integration only for members of a specified test group, or activate for all users.

Duo Premier and Duo Advantage plans: The Device Insight and Endpoints pages in the Duo Admin Panel show which access devices are trusted/managed.
Verify Your Setup
Users with Duo Mobile installed and activated for Duo Push on Android and iOS devices see a device trust dialog when authenticating to a protected resource via the Duo Prompt.

Duo uses the Google Workspace managed device configuration to perform a permissions check to verify device information.

If Duo successfully verifies the device information, and the user has Duo Mobile activated for Duo Push, then the user receives a login request on their phone.

On Android devices, approving the request grants access and returns the user to the protected application. On iOS devices, after approving the Duo authentication request users tap the top-left of the Duo Mobile app to return to the application and complete login. The "Second Factor" logged for these approvals is shown as "Duo Mobile Inline Auth" in the Duo authentication log.

If the user does not have Duo Mobile activated for push, or does not approve the Duo request before it times out, the user returns to the Duo Prompt, where they may select from the available factors to complete 2FA.
Removing the Google Workspace Management Integration
Be sure to unassign your trusted endpoints policy from all applications or remove the "Trusted Endpoints" configuration item from your global policy before deleting an existing Google Workspace integration from "Trusted Endpoints Configuration". You should also disable your Duo admin user in Google Workspace.
Leaving the policy settings in place after deleting a management tools integration may inadvertently block user access to applications.
Troubleshooting
Need some help? Take a look at our Trusted Endpoints Knowledge Base articles or Community discussions. For further assistance, contact Support.
