Announcing Duo MFA Support for AD FS OIDC Applications
The 2.2.0 release of Duo AD FS adds support for OIDC application groups, enabling customers who use Azure Active Directory as their primary user directory to do MFA with OIDC to connect to their corporate cloud applications. This extends Duo MFA to OIDC applications federated with AD FS for users authenticating to those applications.
AD FS
AD FS is a Microsoft identity access solution that gives remote users single sign-on access to protected cloud-hosted applications or services.
It relies on OAuth to facilitate access authentication with application groups such as web applications or APIs.
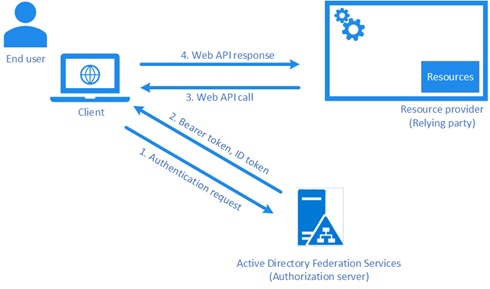
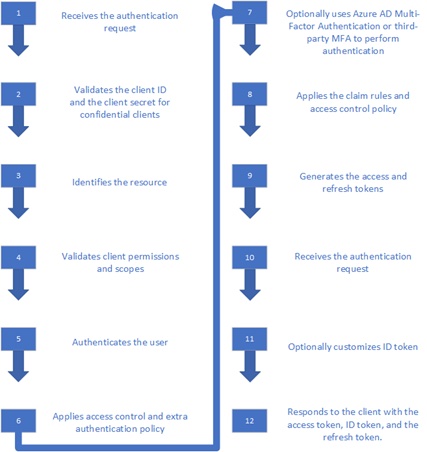
Cisco Duo can be invoked to secure the AD FS access process with multi-factor authentication (see step #7 below):
OIDC
OpenID Connect (OIDC) is an authentication protocol based on the OAuth 2.0 framework. It helps verify the identity of user based on authentication performed by an Authorization Server using REST APIs designed for use in cloud-hosted applications.
What’s new?
Prior versions of Duo ADFS were qualified for SAML 2.0 and WS-Fed relying parties only. Duo’s 2.2.0 release fully supports AD FS MFA access policies applied to federated OIDC/OAuth server applications. Customers who use OIDC application groups in AD FS can now take the next step on the journey to MFA protection featuring Duo Universal Prompt.
For more information on Duo AD FS, see our AD FS documentation. And for specific update details, check out our AD FS 2.2.0 notes.
Summary
Duo’s AD FS MFA adapter offers MFA for all types of federated corporate cloud applications to protect customer environments against attack. Get started today!

