What is Application Security?
Application security, or AppSec, is the consideration and implementation of security measures at every stage of business software development and production. Strong security steps are needed to prevent unauthorized access, data corruption, and other threats that could disrupt an organization or lead to the loss of important information.
Application Development and The Role of Security
Incorporating security early in development, also known as "shifting left", is crucial for creating secure apps. Using a DevSecOps approach makes security a core part of the development lifecycle. This method involves constant teamwork between development and security teams to find and fix potential issues.
DevSecOps focuses on automating security tasks and adding security tools into the development process. This gives developers quick feedback on how their code affects security and helps fix vulnerabilities quickly. It creates a culture where everyone is aware of and responsible for security.
Unlike traditional methods that treat security as a separate, end-stage task, DevSecOps addresses security risks early and throughout development. This leads to safer, more reliable apps and ultimately saves time and resources.
Security Vulnerabilities and Common Application Threats
Injection attackers are a specific breed of bad actor. Like other cybercriminals, they want to steal data or disrupt your digital system. Their specific MO is to inject malicious code into software that then wreaks havoc from within. Some tactics to watch out for include:
SQL injection - Happens when an attacker uses SQL to put harmful code into a server, letting them control the database. This can cause data theft, deletion, or corruption, often due to badly cleaned user inputs.
Cross-site scripting (XSS) - Attackers insert harmful scripts into web apps, which run in users' browsers. This can steal cookies, sensitive information, session tokens, mess up websites, and redirect users to harmful sites.
Security Setup Errors - Common in app security, often from default or incomplete setups, mismanaged settings, and using default accounts, passwords, or keys. These errors can make apps open to attacks like data breaches, privilege escalation, and man-in-the-middle attacks.
Understanding these top app security risks is crucial for developers and security teams to protect the organization. Other common attack methods can be found in the popular OWASP Top Ten. OWASP, or the Open Worldwide Application Security Project, is a not-for-profit application security project dedicated to improving software security through Open Source initiatives and community education. Many great resources and application security best practices can be found on their site.
Best Practices for Enhancing Application Security
Strengthening app security starts with regular code reviews during development. Having multiple team members check the code helps spot potential weaknesses before launching the app. This proactive method prevents future security problems and ensures high security standards.
Using secure coding standards is also vital. These standards set guidelines and best practices for writing code that avoids vulnerabilities and resists attacks.Following these standards lowers the risk of security issues and keeps security measures consistent across the app.
Strong authentication methods are crucial too. Techniques like multi-factor authentication (MFA) and secure password hashing stop unauthorized access and protect user credentials. Better authentication security at the app level greatly reduces the chance of data breaches and unauthorized access issues.
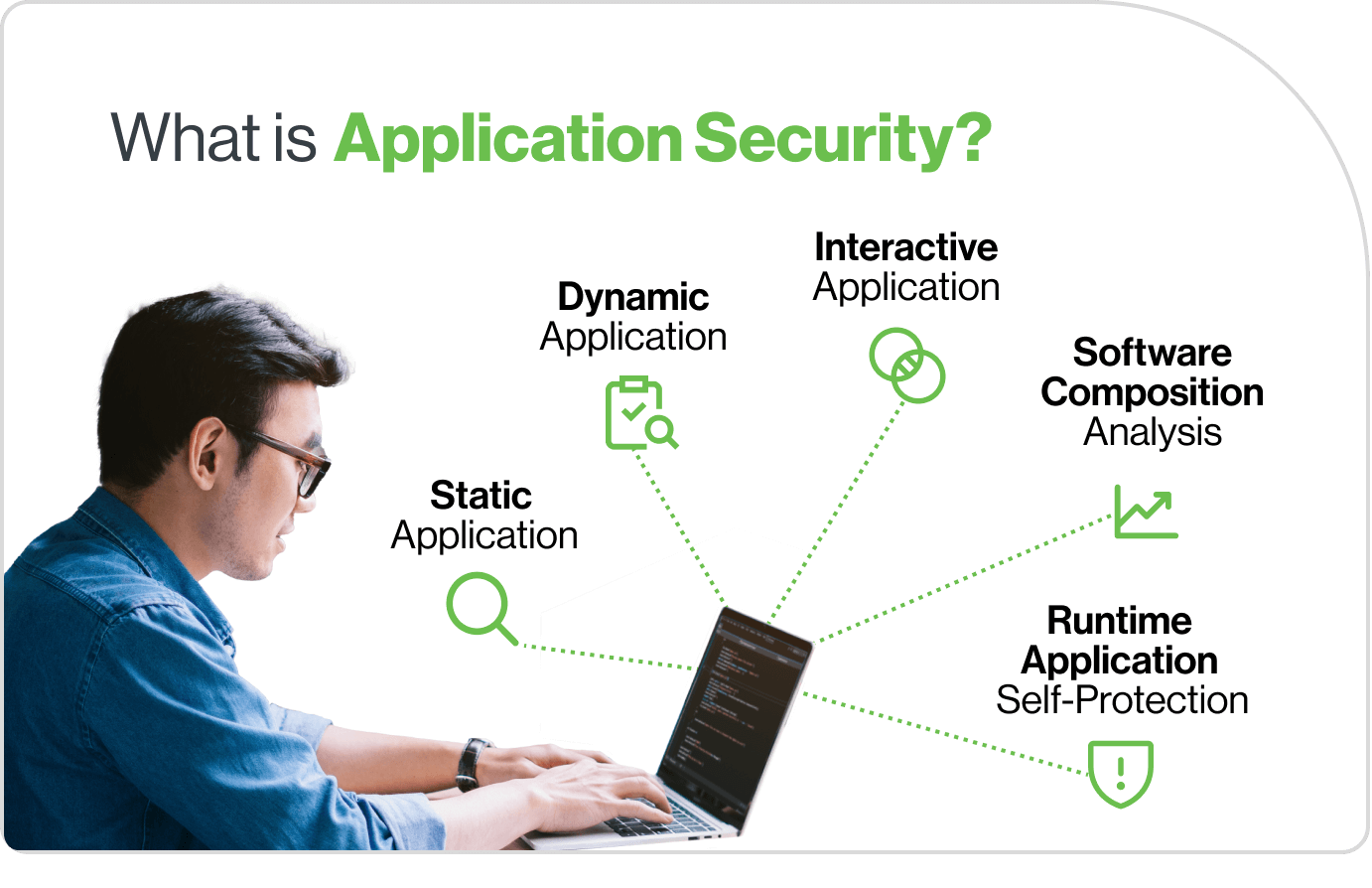
Application Security Tools
Developers and security pros have many tools for identifying application vulnerabilities in apps. These tools find weaknesses, stop attacks, and ensure best practices. They include:
Static Application Security Testing (SAST) - Analyzes source code to find known vulnerabilities and coding errors. SAST tools can spot issues like SQL injection, cross-site scripting, or bad authentication.
Dynamic Application Security Testing (DAST) – Tests apps while they run to find vulnerabilities hackers could exploit. By interacting with the app and watching its responses, DAST tools can spot issues like input validation errors and setup errors.
Interactive Application Security Testing (IAST) - Works within an app during runtime to find security vulnerabilities, combining benefits of SAST and DAST. It interacts with the app's code, detecting security issues in real-time and providing detailed insights into vulnerabilities.
Software Composition Analysis (SCA) - Scans open-source and third-party libraries for vulnerabilities and licensing issues. These tools help track dependencies, detect security risks, and ensure compliance with legal requirements for open-source software.
Runtime Application Self-Protection (RASP) - Detects and prevents attacks in real-time, intervening directly within the app to stop malicious activities. It adds a layer of defense by monitoring app behavior and blocking threats before they exploit vulnerabilities.
Case Study: Learning From Application Security Incidents
History has many examples of insecure apps with big weaknesses leading to major problems for businesses worldwide.
In 2017, Equifax, a big credit bureau in the US, faced a massive data breach. Over 147 million consumers' personal info, like social security numbers and credit card details, was exposed. The breach was due to a known weakness in Apache Struts, a popular web app framework. This caused severe financial and reputation damage to Equifax, with over $700 million in legal settlements.
Earlier, Heartland Payment Systems, a major credit card processor, suffered a breach affecting data from around 100 million credit card transactions. The breach was due to a SQL injection weakness in the company's web app. Attackers used this to install malware and steal payment card data. The breach cost Heartland around $140 million in financial losses, damaged its reputation, and led to legal settlements
Both incidents show the critical need to fix weaknesses in web apps before they lead to massive data breaches with far-reaching consequences.
The Future of Application Security
In the future, we can expect big improvements in app security tools due to advances in automation, artificial intelligence (AI), and cloud-native solutions. Some key improvements include:
AI-Powered Vulnerability Detection and Fixing: AI and machine learning (ML) will be used more to find and fix vulnerabilities in real-time. These systems will learn from past attacks and improve detection accuracy, reducing false alarms. This will allow quicker and more precise vulnerability detection in large, complex codebases, helping security teams by automating repetitive tasks.
Cloud-Native Security Posture Management (CNSPM): As more companies use cloud services, CNSPM tools will focus on securing the application layer. These tools will manage configurations, permissions, and vulnerabilities in cloud-based apps, maintaining security across complex cloud environments. CNSPM will protect cloud-native apps by monitoring and enforcing security best practices, detecting setup errors, and automating fixes.
Advanced API Security Testing: With the rise of APIs in modern apps, security tools will emphasize API security testing. These tools will automate the detection of common API weaknesses like broken authentication, improper access controls, and data exposure. Comprehensive API security testing will reduce risks related to APIs, a key target for cybercriminals in web and mobile apps.
These advancements will greatly help enterprise security teams protect apps, especially in cloud and DevOps-driven environments.
Access Management
Access management combines tools and policy controls to ensure only the right users have access to applications and resources and under the right conditions. Duo’s access management solutions deliver multi-factor authentication (MFA), passwordless authentication, and single sign-on (SSO) capabilities to verify user identities and enforce role-based access. They protect critical resources from stolen credentials and unauthorized access that can lead to systems compromise and data loss.
Explore access management solutions
PRODUCTAdaptive Access Policies For Any Scenario
With Duo, you can apply custom policies based on role, device, location, and additional contextual factors, ensuring control over who accesses what and when.
Learn more about adaptive access policies
SOLUTIONRisk-Based Authentication
Duo's Risk-Based Authentication evaluates potential threat signals at each login attempt and adjusts security requirements, in real time, to protect trusted users and frustrate attackers. This dynamic solution offers granular controls that provide customers with a more nuanced and effective approach toward secure access.
Discover Duo’s Risk-Based Authentication
Frequently Asked Questions
What is application security?
Application security encompasses the measures taken throughout the code's life cycle to prevent gaps in the security policy of an application, ultimately ensuring the application is secure.
Why is application security important?
Effective application security reduces the likelihood of an attack and can help prevent the theft of sensitive customer data.
What are some common application security threats?
Common application security threats include SQL injection, cross-site scripting (XSS), broken authentication, sensitive data exposure, and security misconfigurations.
How can I improve my application security?
You can improve your application security by implementing security measures such as encryption, proper authentication, regular security testing, and staying informed about the latest security issues.
