3 steps to prevent a case of compromised credentials
Oh no! Your passwords are on the internet.
Talks of passkeys, passphrases, and even passwordless all point in one direction: eroding faith in the previously trusty password tucked under your keyboard. Passwords are a weak point in modern-day secure authentication practices, with Verizon highlighting that almost 50% of breaches start with compromised credentials.
In our previous two features, we covered the dangers of phishing (one method of credential compromise) and how to mitigate its impact on users. Today, we cover best practices for an environment that has been compromised.
Compromised or stolen credentials (method unknown) is the second most common type of cybersecurity incident accounting for 27% of reported breaches, according to the Office of the Australian Information Commissioner (OAIC). However, a whopping 59% of cyber incidents involved malicious actors exploiting compromised or stolen credentials, including through phishing and brute-force attacks. If not properly prevented or even detected, losing the “keys to your kingdom” can unlock even more doors for attackers.
What to do when your credentials are compromised
How are credentials compromised in the first place? The answer, like most other cybersecurity-adjacent answers, lies in a combination of factors including social engineering, weak passwords, and other risky security moves or attacks.
Whether it was an accidental phishing link click, news that your password manager was breached, or a depressingly robotic text from your telecom company, compromised credentials and data leaks can quickly become a vector for larger attacks.
1. Immediately let the IT or security team know of a potential credential compromise
According to the OAIC, a key objective of the Notifiable Data Breaches (NDB) scheme is to protect individuals by enabling them to respond quickly to a data breach to mitigate the risk of harm. Delays in identifying, assessing, and notifying breaches make it more challenging to prevent harm.
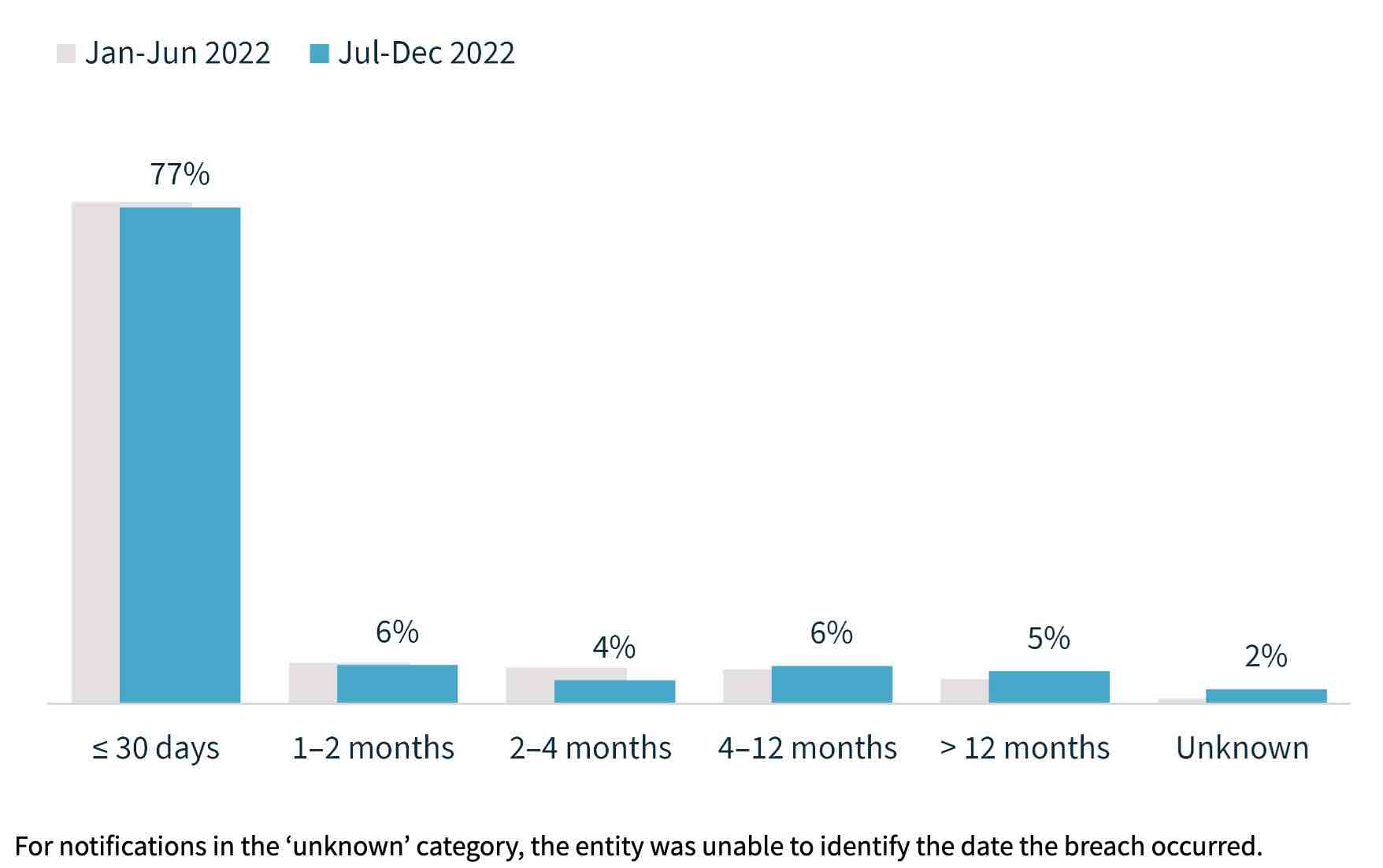
Luckily, the average time taken between an incident occurring and being reported has decreased, with 77% of compromises identified within 30 days. But the 33% of compromises not detected immediately can take more than 200 days to discover. That gives attackers roughly 6 months to establish a foothold on a network, access sensitive data, and disrupt business activities.
Immediate notification can also help trace other potential compromises. Aside from the possibility that attackers may not immediately turn around and use the data or credentials, the Privacy Act requires Australian entities to notify individuals about an eligible data breach, including certain information about the incident, as soon as practicable.
2. Change your passwords and upgrade to stronger authentication methods
Passwords have long been the primary method of authentication for online accounts, but as cyber-attacks become more prevalent, it's clear that they alone are not enough to protect against modern threats.
User-generated passwords can be deceptively weak, with less caution given to password management as remote and hybrid work become more common. But no matter the frequency employees are pressed to reset, add some numbers, and inevitably forget their new password, the shift to ditching them completely is not yet a path fully paved. Oftentimes, the journey to passwordless starts with providing this functionality to a few key functions within the organisation—IT Admins, for example—or nominating a few critical apps that will have passwordless access. Until a fully password-free environment is deployed, accepted, and adopted by all users, less secure methods of authentication will still be relied on.
These habits highlight the need for more modern password technology and stronger authentication methods.
Types of stronger authenticators
Biometrics and FIDO2 are both examples of stronger authenticators that can help to secure online accounts from the impacts of credential compromise. While passwords can be easily guessed or stolen, biometrics provide a more secure method of authentication. In fact, the 2022 Trusted Access Report measuring 49 million devices reported that 81% of phones have biometrics enabled, presenting the potential for a stronger security posture for Australians.
Will we ever get rid of passwords completely? Likely not immediately. Cisco CISO Wolfgang Goerlich highlights the case for why passwords are kept around in The Life and Death of Passwords:
"In an ideal world, we say goodbye to passwords altogether. They don’t work. We’ve got six decades of proof of that. But along that way in six decades, we’ve built up a lot of systems, a lot of systems that have passwords, a lot of infrastructure. When organizations go through modernization, they don’t replace everything. There are use cases that will still need passwords into the near future—such as shared accounts, system accounts, service accounts—and so for a variety of reasons, a password is going to persist." — Wolfgang Goerlich
Of course, the answer to stronger authenticators doesn’t have to be so black and white. While passwordless rises as a strong but novel secure access option, one cybersecurity measure has already become an enforced default.
3. Enable multi-factor authentication
As best described by Global Advisory CISO Dave Lewis, “We have now arrived at a turning point with respect to cybersecurity. It has become clear that MFA is basic ‘you must be this tall to ride the rollercoaster’ for any [organisation].”
Duo reported 13 billion authentications worldwide in 2022, an increase of 41% from the year past. In Australia, authentications increased by 14.1%. Whether by pre-emptive risk-reduction or compliance-driven action (case-in-point: the latest Essential 8 guidelines and rising cyber liability insurance costs), multi-factor authentication (MFA) is quickly becoming a standard tool in our security toolkit.
What some people miss, however, is that corporate-mandated authenticators can and should also be enabled for personal accounts. For example, the Duo Mobile app can easily be set up as an additional layer of security for your social media, email, password managers, investment apps, and even third-party video game accounts. Because the app acts as a secure container for authentication codes, no credentials are shared with either Duo or your company.
Picking on someone…credential compromise in Australia
It goes without saying that a lack of MFA puts your company or personal accounts at risk.
In 2022, a large-scale data breach was reported at a major Australian health insurer resulting in the compromise of sensitive personal information belonging to millions of customers. The breach allegedly gained initial access through high-authority credentials that were compromised and then sold on the dark web and hadn’t been stopped by an additional MFA check. It is believed the attacker took their time after gaining access, performing reconnaissance.
As a result, about 3.9 million records including details such as names, addresses, dates of birth, and other sensitive information were exposed. In addition to the hefty $25 to $35 million cost to the affected health insurer, the breach now puts individuals at risk of identity theft and other fraudulent activities. Though not infallible, having effective MFA in place can be both a preventative pre-breach measure and a protective post-breach security layer.
Two-factor authentication is a foundation, not a silver bullet
The risk of credential compromise is no longer an if but a when.
MFA, once a step-up method of security around mission-critical assets, has now become a baseline for secure access into and within an organisation. However, that's not to say that a second factor, say an SMS passcode, suddenly becomes an impenetrable line of defence.
Despite the benefits, some employees may still resist MFA, believing it places an unnecessary or annoying barrier between them and the information they’re trying to get. Adding to our phishing list, push-phishing is a rising method of attack that takes advantage of a user’s MFA fatigue intending to circumvent the additional identity-confirming methods in place. Users are tired of alerts, and their push fatigue can create security vulnerabilities.
While FIDO2 offers the gold standard for authentication, not everyone can implement this today. Shipping security keys to all users can be expensive and an organisation’s users may not have access to devices with biometrics.
Therefore, Duo has taken steps to put businesses in the best possible position to prevent these common attacks by meeting them where they are, today.
Options for stronger MFA
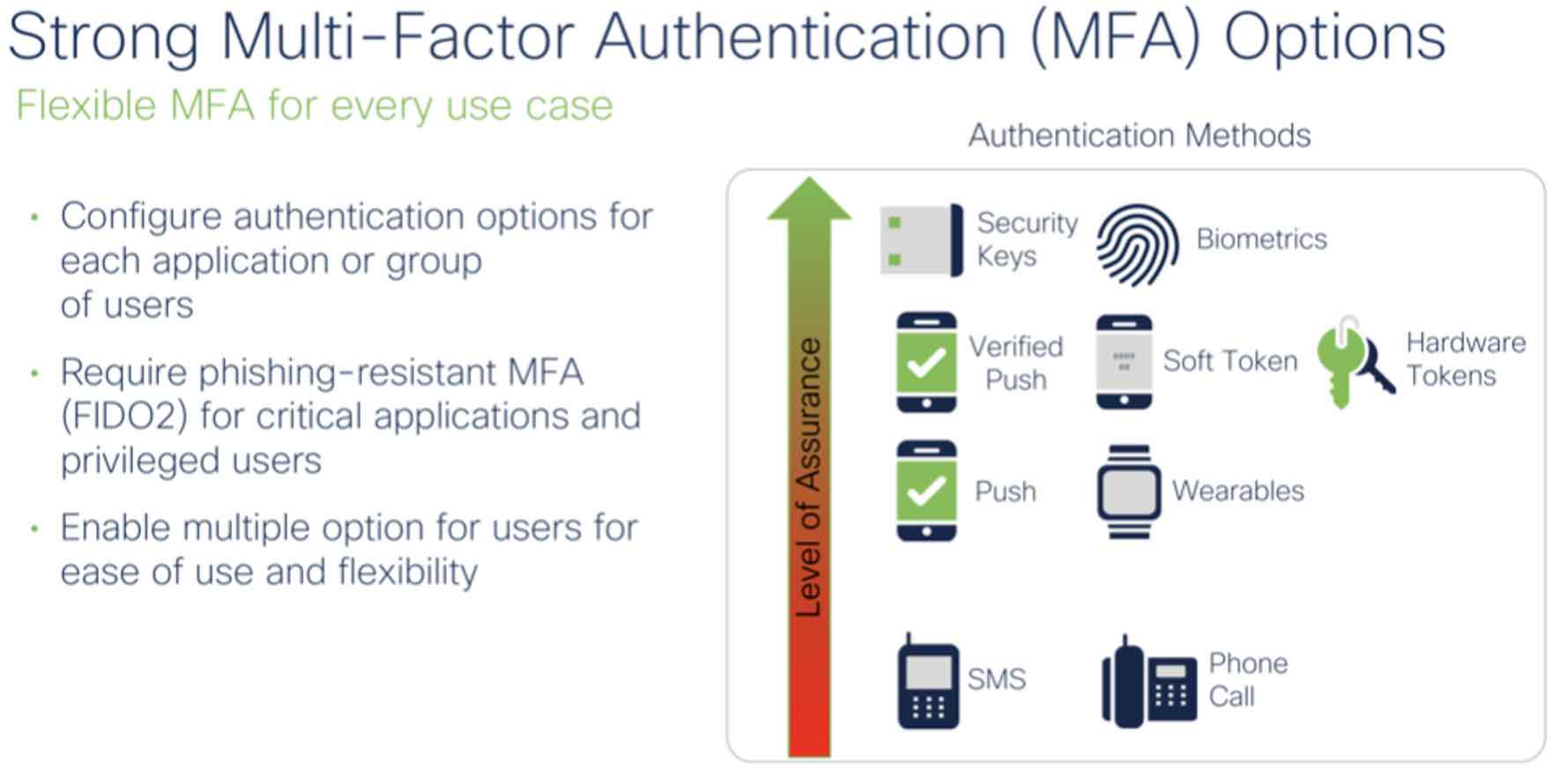
Authentication methods have a gradient of security—methods like biometrics and number matching verified push outranking simple push notifications or SMS.
Verified Duo Push requires users to enter a code in the Duo mobile application to better protect against push phishing attacks enabled by compromised credentials. With a standard push-based MFA solution, a persistent bad actor could still gain access to the company network. However, with Verified Duo Push that same attack is immediately stopped because the bad actor is unable to complete the transaction - they cannot enter the unique code in the Duo mobile app, and the employee is encouraged to alert their IT team with a fraud report.
Risk-Based Authentication
Any new end-user security deployment plans must also consider: how many hours do I want to spend on set-up, complaints, and help desk tickets?
Higher-friction authentication methods are impactful when used intelligently; after all, the goal is to frustrate push-fatigue attackers, not punish an employee for working out of a coffee shop. Risk-Based Authentication (RBA) focuses on this philosophy.
To address how attackers have evolved, Duo RBA assesses user and device telemetry to make decisions about which logins are most suspicious and present a credible risk to an organisation even after the initial login.
Known attack patterns such as push spray, unrealistic travel, and MFA fatigue flag only the highest-risk authentications without causing undue friction for users
Patent-pending Wi-Fi Fingerprint protects user privacy while also reducing friction and saving time, using anonymised Wi-Fi network information instead of less reliable IP addresses
Use machine learning to surface risky authentications and device registrations that need security teams’ attention
Step up authentication requirements for users when they are enrolling new devices
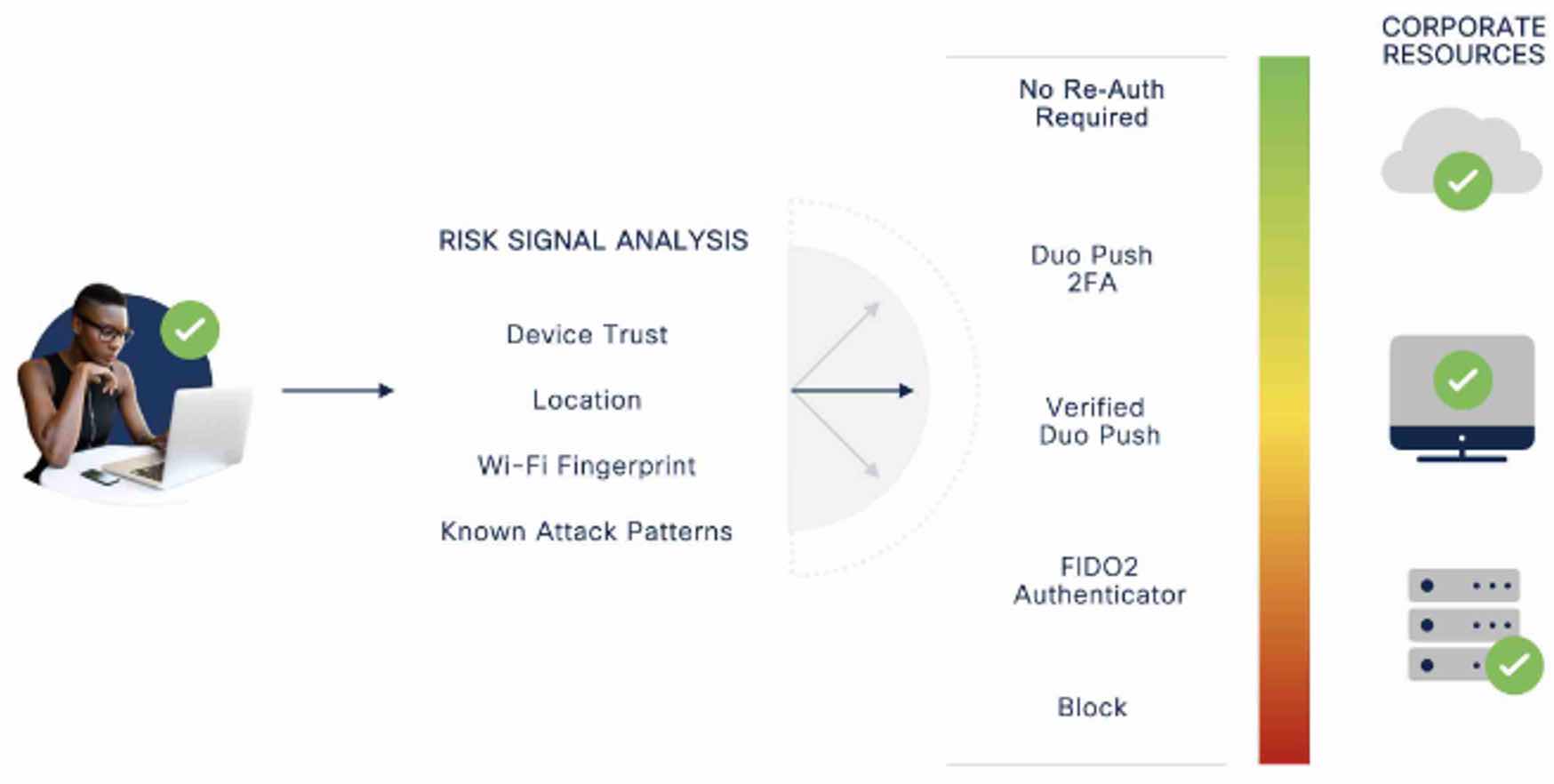
Only with higher-risker logins are users prompted to step up and prove their identity. On average, a step-up to a more secure factor is required about twice in every 1,000 authentication attempts.
Duo also makes investigating and reporting potential breaches straightforward and easy to access.
Duo’s API solution allows increased visibility into enrolment actions, fraud and threats, such as registering a new phone or hardware token or creating a WebAuthn credential
The Duo Admin Panel enables IT admin to generate reports through by-the-minute log data on device health, impact of granular access policies, and authentication patterns
Cisco Identity Intelligence evaluates data from real-world attacks to highlight potential risks by parsing through security events and surfacing those that appear fraudulent
Risk-Based Authentication plays a key part in continuously evaluating and adapting to a user’s behaviour as they go about their workday. This builds towards continuous trusted access—a security practice of assessing and responding to risk at different points in the user journey, from enrolment and beyond, and even within a user’s day.
MFA plays a preventative role in keeping unauthorised users and devices out of the network, but continuous visibility and analytics into authentication and network behaviours fosters proactive detection of potential breaches. Finally, the ability to generate logs and records assists in decreasing incident response times.
What’s next?
The persisting practise of keeping passwords around poses not just a technical, but also a very human and habitual hurdle in the journey of adopting passwordless and protecting against cyber-attacks. However, with the adoption of stronger authentication methods, such as biometrics and passkeys, and the implementation of smarter secure access solutions, Australians can improve their cybersecurity posture and protect themselves from the increasing threat of cyber-attacks.
Phishing and compromised credentials reveal the importance of strengthening the “keys to the kingdom” and equipping users with security best practices. But once the keys are compromised, what are attackers ultimately looking to achieve? In the final instalment of this series, we cover one of the most dangerous and rapidly scaling financial motivators for cyber attackers: ransomware.
Learn more:

