Cisco Security Democratizes Extension Security for Firefox and Edge
Two years ago, we released CRXcavator (pronounced crux-cavator), a free tool that examines the security hygiene and risks of Chrome extensions, looking at criteria such as permissions and security policy, and empowers users to make informed decisions about the extensions they use. Originally released as a Duo Labs project, CRXcavator is now provided by the same team within Cisco Security.
Over the last two years, CRXcavator has helped make the browser ecosystem safer and more transparent by providing developers, users, and organizations with consistent and consumable information regarding potential extension security risks. Security teams at organizations such as Lyft and Datadog have adopted the tool as part of their security strategies; researchers have used CRXcavator to help Google uncover and take down hundreds of malicious extensions; and hundreds of thousands of security conscious users have utilized the tool to in their personal and professional lives to improve their security posture.
After democratizing extension security for Chrome, we are thrilled to announce a major update to CRXcavator that adds support for Mozilla Firefox and the beta version of Microsoft Edge Add-ons site. This addition greatly expands the scope and accessibility of the tool and more thoroughly secures users. CRXcavator will now continuously scan the Firefox add-on and Edge extension store as it does for Chrome, generating and updating CRXcavator reports for all extensions, as well as scanning for newly-added ones as they become available.
This enables the tool to provide up-to-date security assessments with a potential risk score, alerting the user to possible red flags and risks that extensions may introduce. We’ve also updated the user interface to ensure consistency across reports.
Why Extension Security?
Browser extensions have an incredible amount of access to user data and, if not properly accounted for, can quickly become a security blindspot. Earlier this year, a browser extension used by millions of users was removed from the Chrome Web Store for containing malware. “The Great Suspender,” as it was named, had been recently sold by its old maintainer to an unknown third party with malicious intent; the new maintainers added potentially malicious code and a new permission.
This prompted Chrome to ask users to accept the new permission which alerted the community and ultimately pressured the new maintainer to revert the change. The extension stayed under the new maintainer’s control over the extension until Google blocked and removed it from the Chrome Web Store in January. The downfall of this once-trustworthy extension and the risks it was able to introduce in a short amount of time demonstrates that browser extension security is an important issue in today’s evolving threat landscape, and that users and organizations must remain vigilant.
We launched CRXcavator with this exact problem in mind. However, Chrome isn’t the only browser that allows extensions the option to access large amounts of user data. The Great Suspender was available on Microsoft Edge alongside Chrome, and in January 2020 Firefox was found to have potentially malicious add-ons.
State of the Web Stores
Back when we first launched, we scanned 120,463 Chrome extensions to see what unsafe practices might be exposing organizations to risk. This number has since increased to 165,365 Chrome extensions and apps.
Chrome Ups and Downs
Since we last compiled our metrics on the Chrome Web Store in 2019, Chrome has taken steps to improve the security of its extensions and encourage safer practices among creators.
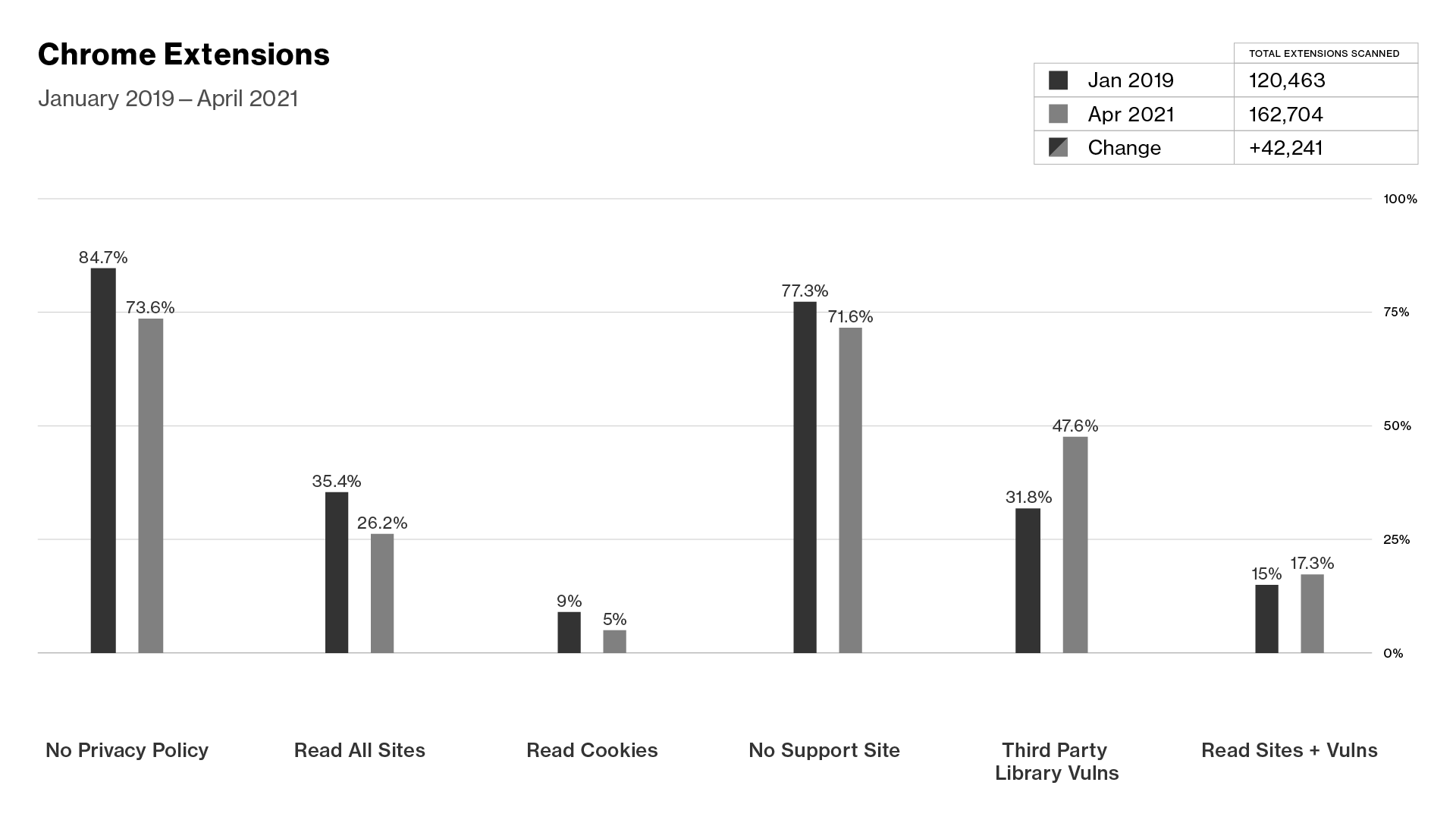
There have been a few particularly noteworthy changes that signal a positive shift in the Chrome extension safety. We’ve scanned around 42,000 new Chrome extensions over the past two years and found that overall, a smaller percentage of scanned extensions read your data on any site and cookies compared to 2019. Additionally, a larger percentage provide users with a privacy policy and a support site to contact.
However, some areas did not improve. A significantly larger percentage of extensions use third-party javascript libraries with publicly known vulnerabilities as detected by RetireJS, and a slightly larger percentage have both publicly known vulnerabilities and can read your data from any site, as shown in the chart below. Although this may seem like a significant increase, it may just be a consequence of RetireJS finding new vulnerabilities in existing extensions over time and not a dramatic shift in the number of developers adding outdated third-party libraries to their extensions.
Firefox & Edge
In addition to scanning 162,704 extensions for Chrome, we’ve scanned 20,520 Firefox Add-Ons and 4,373 Edge Extensions for similar problems. It is important to note that the Microsoft Edge add-on site is still in beta at the time of this report and we expect that Edge extensions will continue to evolve in ways that include management of extension security risks. Edge currently has a much smaller population of available extensions compared to Chrome and Firefox. This must be taken into consideration when comparing Edge with Chrome and Firefox as it is too early to identify comparable trends and it is more likely that actions taken by developers or Microsoft, such as waves of new extensions or removal of extensions due to abuse, will have an outsized effect on the overall percentages.
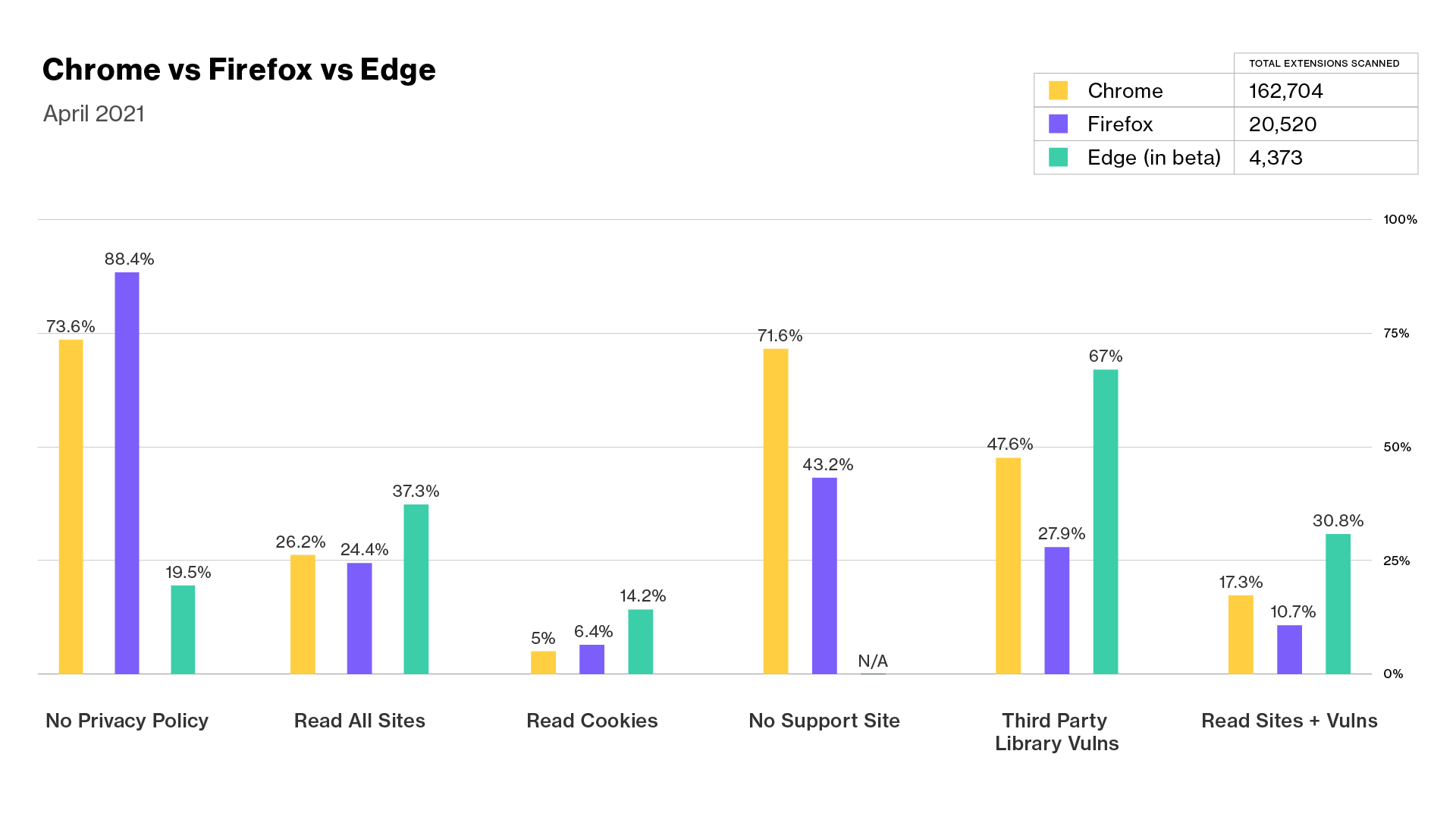
Like Chrome, a majority of Firefox extensions have no privacy policy. However, of the Edge extensions scanned, ~80% of Edge extensions do have a privacy policy. Edge has far fewer extensions compared to Firefox and Chrome, many of which are from well-known developers and more likely to have a privacy policy. We will see if this continues to hold true as the Edge ecosystem expands and more smaller developers are added.
While Edge beats Chrome and Firefox in extensions having privacy policies, a higher percentage of them contain known third-party vulnerabilities — twenty percentage points more than Chrome and more than twice as high a percentage as Firefox, which does the best of the three browsers in this category. It’s also interesting to note that of the Edge extensions that can read your data on any site, 82% of them also contain third-party vulnerabilities; this stands in comparison to Chrome where about two-thirds of the extensions that read all data contain vulnerabilities and Firefox where less than half do.
Knowing and comparing these numbers can help users stay alert as they decide how they approach the use of extensions with their preferred browsers.
New Look, Same CRXcavator
In addition to adding support for Firefox and Edge extensions, we’ve made some changes to the UX. We’ve redesigned the style of various elements to modernize the look and feel and to improve thematic consistency, focusing many of the changes around enabling analysis of extensions for the Firefox and Edge browsers in addition to Chrome.

We’ve also overhauled multiple pages, most notably the extension report. The report now presents the same data in fewer sections, making better use of available space and shortening the overall size of the report page, improving the experience on both desktop and mobile. Users can also more clearly see the extent to which various sources of risk in the extension contribute to the overall potential risk score.
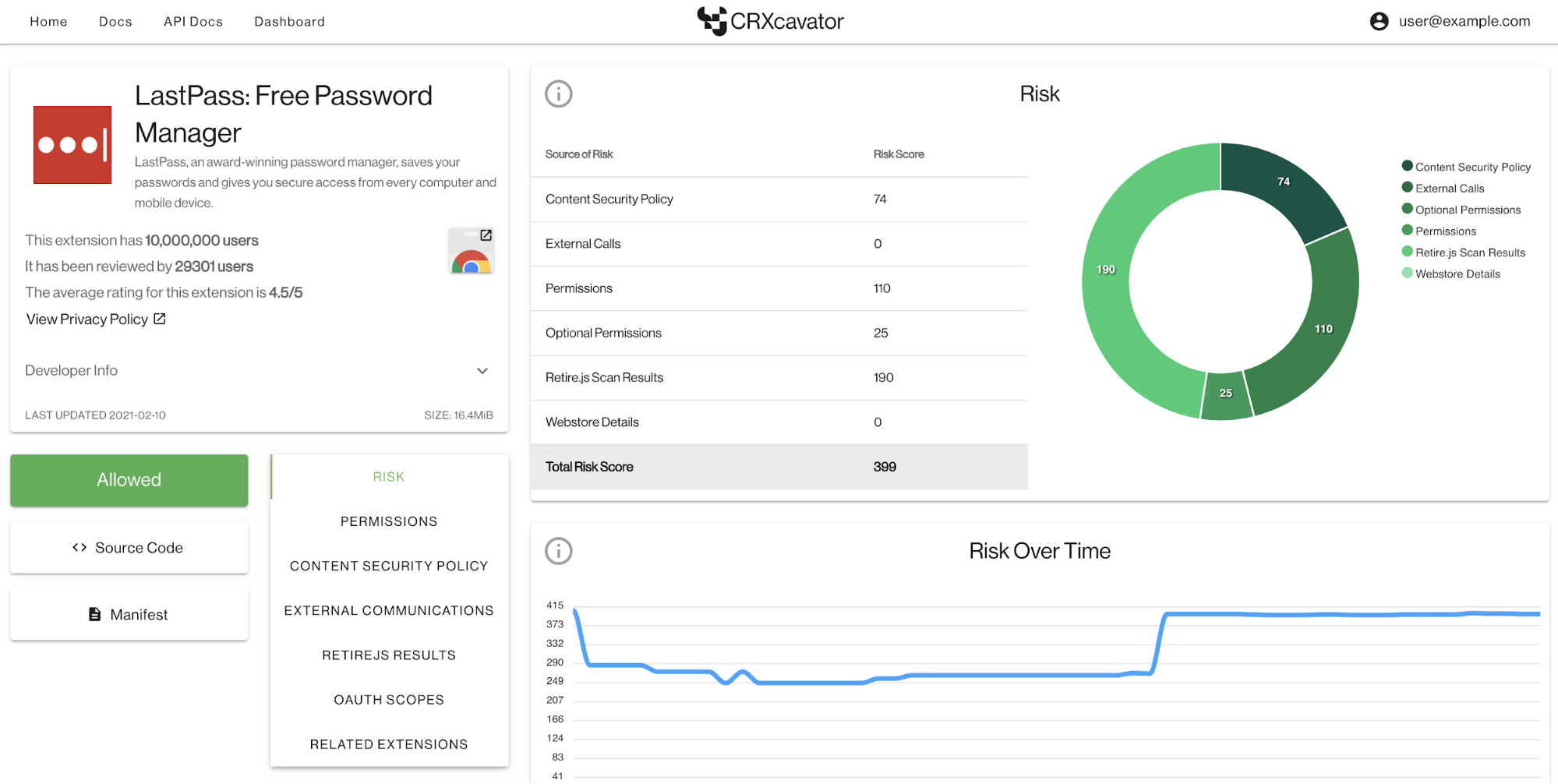
These reports will mostly display the same or corresponding data that CRXcavator’s Chrome extension pages do — each store provides information differently. For example, Firefox and Edge do not provide permission warning data via their API as Chrome does, so we’ve redesigned and updated our UI to make reports across browsers more consistent, comparable, and accessible.
Users will be able to view Firefox and Edge extension reports, but will not be able to add extensions to their group’s explicit allow list; CRXcavator Gatherer, our browser extension on the Chrome Web Store that gathers the inventory of extensions installed across an organization, is not currently available on Firefox or Edge but may be added in the future based on demand.
What Does the Future Hold?
We look forward to seeing Google, Mozilla, and Microsoft continue to make strides towards securing their browser extension stores and encouraging better extension safety standards. We’ve spoken in the past about Google’s Manifest V3. Edge, which is based on Chromium, automatically inherits this standard, and Firefox is implementing their own version of Manifest V3. All of these new Manifest versions include provisions to prevent extensions from incorporating remotely hosted code which could be used to evade malware detection.
Additionally, Google has implemented a new privacy requirement for their extensions. As of 2021, extension developers are required to list the type of data they collect from users. This information is displayed on the Chrome Web Store for users to see when deciding whether to install an extension. To help their users make more informed decisions when evaluating extensions, Firefox has published a great resource that guides people through the questions they should ask when deciding to install an extension.
As Chrome works toward transparency in browser extension security and other browsers take their own steps to secure their web stores, CRXcavator will continue compiling this information and staying up-to-date to ensure that users have the most detailed information possible to make informed decisions about their browser’s extension security.
While big strides have been made in browser extension security since CRXcavator was first developed in 2019, users must continue to audit their extensions and keep an eye on privacy concerns and policies to avoid potential security breaches and keep their data secure. We’re always looking for ways to improve CRXcavator for individual users and organizations, and we’ll continue to update CRXcavator as the needs of browser extension security and our users evolve.

