Advanced Phishing 201: How to Prevent Phishing from Impacting Your Users
With advanced language-based AI tools like ChatGPT growing increasingly accessible, the battle to prevent phishing attacks from impacting users is no longer answerable with just one security solution.
Why is layered security essential against phishing?
Effectively protecting complex networks against sophisticated phishing attacks involves a comprehensive security stack including multi-factor authentication (MFA), single sign-on (SSO), and domain name system (DNS) security.
As mentioned in our previous post breaking down what modern-day phishing attacks look like, experts recommend that a layered approach to security can prevent single-point vulnerabilities and catch the most phish.
However, it isn’t easy for security programmes to go from zero to one hundred in any organisation, especially when it comes to the people impacted. In an environment with constant turnover of thousands of users, Australian educational institutions like Deakin University and others around the world turn to multiple solutions to secure against phishing.
Reduce reliance on passwords with single sign-on and MFA
Nobody ever appreciated opening an exciting email just to find out their company had bamboozled them with a fake phishing test. In a study of corporate phishing training conducted over 15 months with 14,000 participants, researchers found that embedded training during simulated phishing exercises, as commonly deployed in the industry today, does not make employees more resilient to phishing. In fact, it instead can have unexpected side effects that make employees even more susceptible to phishing.
A shifting IT environment also contributes to complexity and expanding attack surface. An increasing number of authentications are attributed to cloud applications, with a 24% rise in the percentage of cloud app authentications in 2022. As a result, organisations have turned to single sign-on solutions to decrease the number of credentials needed to access various cloud and on-premises applications.
The University of Queensland, for example, used Duo to secure their single sign-on portal to safeguard the cloud and on-premises apps users needed to access.
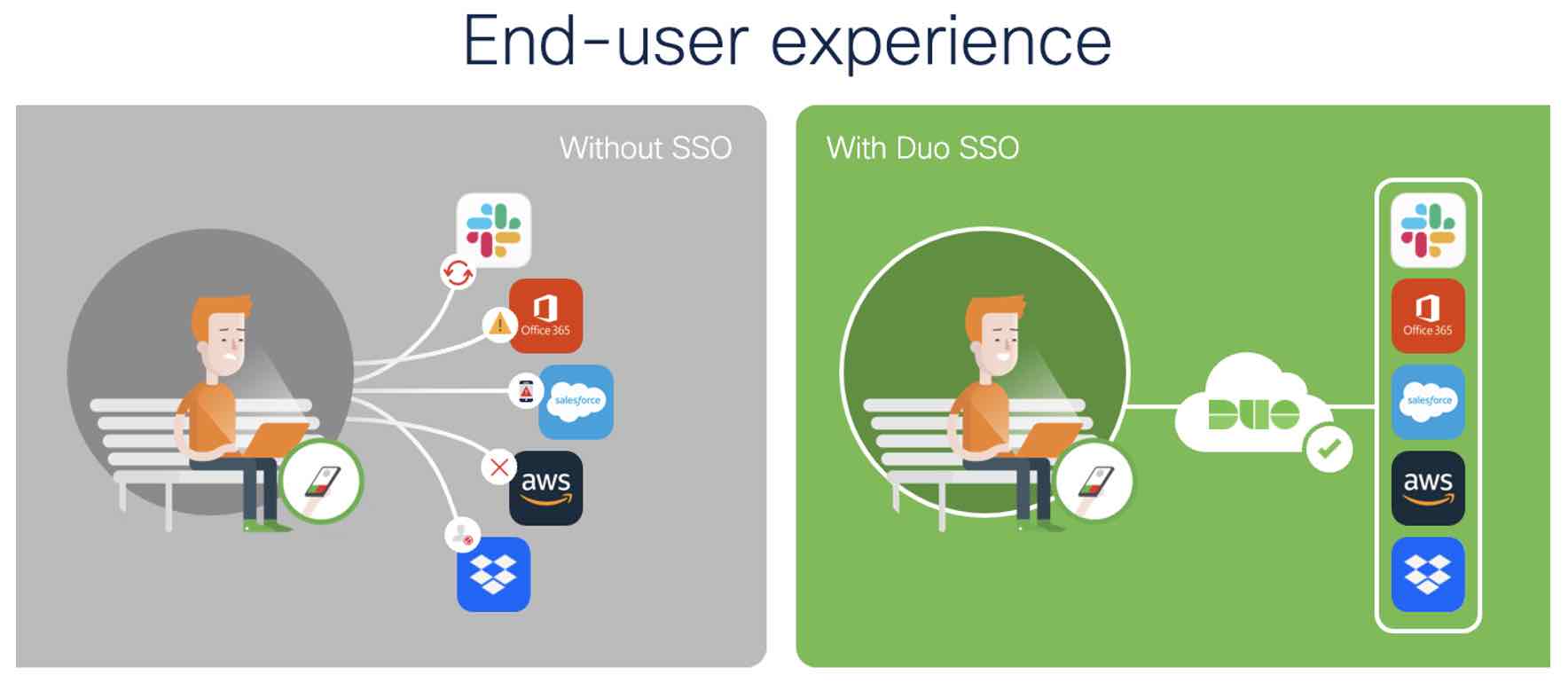
Rather than making users feel guilty for being gullible, single sign-on (SSO) solutions like Duo SSO complement MFA to mitigate phishing risks by enabling users to use a single set of credentials to access multiple applications. Additionally, Duo SSO helps:
Reduce the risks associated with credential compromise and breaches by decreasing the number of credentials a user needs to access the applications they need
Enable users a secure and stress-free login experience to permitted cloud and on-premises applications, including those built on SAML 2.0 and OpenID Connect (OIDC) standards
Adopt self-service capabilities to help IT and helpdesk teams save time and costs related to onboarding to applications, password resets, device management and more
Enforce least privileged access through granular access policies to limit user access to just the apps they need, preventing lateral movement
More easily adhere to regulatory compliance requirements (e.g., PCI DSS, HIPAA, etc.) for verification of users
Duo's single sign-on solution can help increase user productivity. Instead of entering credentials each and every time they need to access an application, students, faculty and hospital staff can log in just once using Duo's SSO to access various cloud applications from a single dashboard, using their existing credentials and strong MFA.
Reducing the number of credentials by adopting SSO ultimately minimises the risk of losing those credentials to phishing attacks.
Stepping up: How email, DNS, and MFA security can protect users from phishing
Phishing links are commonly sent to the target through email messages. Case-in-point, we’ve all heard of the classic Nigerian prince scheme. However, these messages, powered by natural language AI models, are getting craftier—prompting users with false but convincing “you received a comment on your last document” and “please download this update ASAP” polished correspondences.
Luckily a secure email gateway like Cisco Security Email Threat Defense can prevent these messages from even landing in your inbox. With Email Threat Defense, all inbound, outbound, and internal email is scanned for spam, viruses, and anomalies that might indicate incidents of compromise or phishing attempts.
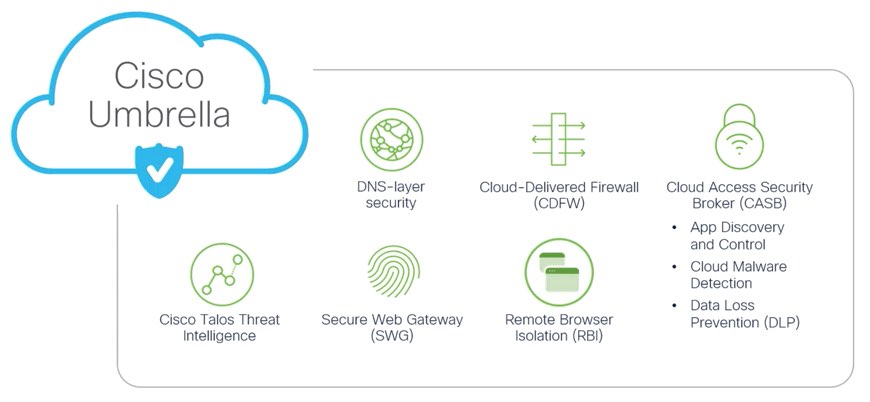
But if a user’s personal email or just unguided surfing leads them to click on a phishing link, a DNS-layer security solution like Cisco Umbrella will block the connection, log the threat, and notify the user appropriately. Domain name system security (DNS) is another layer of protection that stops users from ever opening fraudulent links. Cisco Umbrella (DNS solution) secures all the outbound traffic from an organisation to determine where it is going on the internet.
Umbrella also includes threat intelligence, remote browser isolation (RBI), data loss prevention (DLP), and cloud malware detection, all while acting as a secure onramp to the internet to provide protection against threats for users anywhere they connect.
When combining these defences with Duo’s secure authentication solutions, businesses can prevent unauthorised access, decrease the risk of lateral movement, and protect their users and data wherever they are.
Deakin University catches a malicious attack attempt
Faced with rising audit demands, 100,000 devices and users accessing the network daily, Deakin University looked to Cisco to implement solutions to improve their security posture.
“We are a small team, coming from a very low-maturity security function and ad hoc processes here and there,” explained Fadi Aljafari, information security and risk manager at Deakin University. “We didn’t have a reliable security capability or any sort of architecture for our security offering.”
The team began building out an architecture including Cisco Umbrella, Cisco Email Security, and Cisco Duo. As they added new solutions, they could identify security weaknesses and develop a defence-in-depth, integrated approach to information security. And with Cisco’s XDR threat response integrated across their security solutions, analysts have unified visibility and can investigate threats from a single console.
Altogether, the University reduced response time to malicious emails from an hour to as fast as five minutes, even catching a nationwide attack one week prior to the prime minister’s alert. Previously, it would have taken at least a week to investigate.
“Using the security products from Cisco, in one hour we were able to search all our network and block all the indicators of compromise from a single application. We didn't even need to switch screens.”
As an additional result, Deakin University saw improvements in compliance with the NIST cybersecurity framework and Australia’s ACSC Essential Eight Maturity Model. After implementing Cisco solutions, Deakin went from 20% compliance with NIST to 68%, with a target of 85% by 2022. Likewise, the university raised its ACSC model maturity level for most of the strategies on mitigating cybersecurity incidents.
With a combination of email security, DNS protection, and advanced MFA, these universities have been able to reduce their phishing attack surface area whilst ensuring compliance with data protection regulations.
Zero Trust: Everyone is the perimeter in a hybrid world
An increasing number of authentications are coming from crevices of the web, around the world, and across the cloud. It's clear that the hybrid world of on-premises and cloud-based services is here to stay, and so the expanded attack surface requires expanded protection—especially when it comes to users.
When there are no borders, everyone is an insider, which dramatically increases risks across every aspect of business. This is the fundamental “why” for a zero-trust security strategy, built on the following principles:
First, accurately establish trust. Strongly verify user and device trust before granting access.
Second, consistently enforce trust-based access based on the principle of least privilege.
Third, because change is inevitable, continuously verify trust, and instantly adjust access based on risk.
And fourth, dynamically respond to change in trust, and then investigate and orchestrate incident response.
In higher education institutions, one user can have several different (and shifting) roles that complicates assigning user-based access policies. For example, a research assistant may be both a student and a faculty member—just to become an alumnus the following year. Enforcing the principle of least privileged access through features like group-based granular application access policies is much more of a challenge.
User experience must be top-of-mind for security changes, especially as identity is the new perimeter. Duo’s user-friendly and strong access management solution kicked off the University of Queensland’s zero-trust strategy, whilst Deakin University bolstered protection with Cisco’s security portfolio. Customisable multi-factor authentication and a comprehensive DNS security solution are fast to cloud-deploy and quick wins towards a zero-trust security strategy.
What’s next?
From our passwords leaked (and, accordingly, for sale on the dark web), to phishing emails (with PII on the hook), to ransomware (we all know this one) — it feels as though the list of cyber scaries grows longer by the day.
While more sophisticated anti-phishing techniques evolve, two other breach types still make up a significant proportion of cybersecurity headaches. In the next instalment of this series, we’ll break down the second most common breach according to the OAIC: When users bite the hook and credentials are, unfortunately, compromised.
Want to learn more about how to prevent phishing?
Check out the University of Queensland and Deakin University customer stories to see how these organisations deployed Cisco Security solutions to protect users from phishing attacks. Then, check out our ebook Duo for Essential Eight to see how Duo can help your organisation reach ACSC Maturity Level 3.
Trying to understand how to roll out a layered approach to cybersecurity? Be sure to download our ebook Why Multi-Factor Authentication Demands Single Sign-On.

