The FBI has issued a private industry notification to the healthcare industry, warning organizations that attackers are actively targeting FTP (File Transfer Protocol) servers to access protected health information.
These FTP servers are connected to medical and dental facilities, giving attackers access to regulated and sensitive protected healthcare data, according to the FBI. Criminals could also configure FTP servers to allow for write access, giving them a tool to store or launch malicious attacks.
FTP allows for basic, unencrypted and anonymous public file transfers, using cleartext passwords for authentication, according to SSH.com. While the legacy protocol has been replaced by SFTP and SSH, the implementation is often forgotten by organizations as it is deployed years ago, but never disabled or replaced with a more secure protocol.
The FBI cited research from 2015 about over one million FTP servers that were configured to allow for anonymous access to data stored on the servers, according to a University of Michigan report. Last September, Softpedia reported that nearly 800,000 FTP servers available online via an IPv4 address were accessible online without the need for any credentials.
Exposing databases of private patient information can lead to HIPAA violations which come with hefty government fines and data breach costs.
At this year’s RSA Conference, it was reported that the estimated annual costs of data breaches affecting the healthcare industry has topped $6 billion, with an average cost of $2.1 million to resolve breaches, based on a Ponemon Institute study on healthcare data privacy and security.
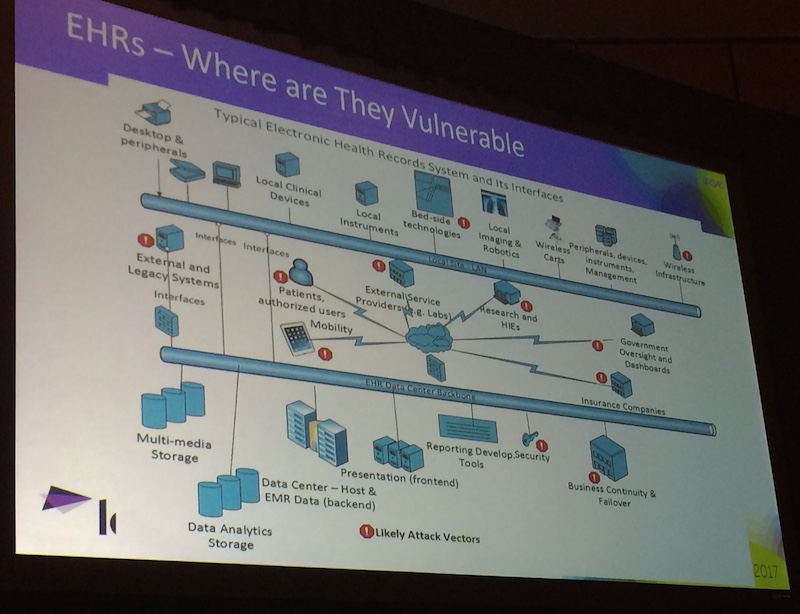
In the talk about electronic healthcare record (EHR) security, a diagram about where EHRs are vulnerable highlighted external and legacy systems connected to EHR data centers as likely attack vectors, for good reason.
Any legacy software can introduce a point of weakness for healthcare organizations. In the 2016 Duo Trusted Access Report, we found that the healthcare industry is even more behind than other industries on average when it comes to updating their Windows operating systems. Only 14% of Windows endpoints in healthcare were running the latest version, Windows 10.
We also found that the healthcare industry had twice as many endpoints running Windows XP, a 16-year-old version of the OS that no longer receives security updates.
Updating legacy software can sometimes be difficult, if not impossible, due to application dependencies and interconnected medical devices. However, the costs and impact of a data breach can be far greater than those associated with updating, patching and replacing old systems with more secure ones.